April 5, 2024
Many legal professionals are proficiently familiar with the discovery portion of matters since this work, which involves collecting and managing hundreds of gigabytes, sometimes terabytes, of data, can be quite arduous and require tight collaborative support from highly organized eDiscovery specialists. In comparison, however, the equally critical process of preparing for trial that lawyers manage upon filing a case is not as universally known to the eDiscovery community since these tasks and workflows are typically administered and overseen by different legal case teams.
March 28, 2024
The concept of infusing Artificial Intelligence into legal technology solutions started at the onset of the digital age, around the time when smartphones became widely available and AI began to be practically applied to optimize user experiences based on prior user behavior. Brands that rushed to develop and incorporate AI into their products and services included global flagship companies such as Amazon (Alexa), Apple (Siri), and subscription-based organizations, Netflix and Spotify, that began to feature the ability to provide AI-based recommendations to users.
December 25, 2023
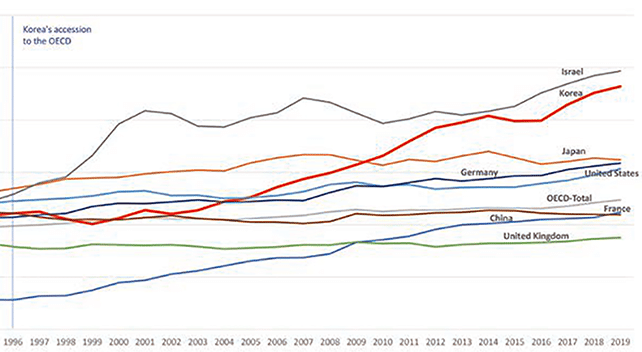
Global technology competition has grown fierce recently requiring nations to consider and enact technology protection policies and strategies. In Japan, for example, there was a significant change in 2014 under the Liberal Democratic Party that led to the development and passage of the Economic Security Promotion Act in 2022, along with a new National Security Strategy.
October 12, 2023
In this blog, we will discuss a few key challenges associated with handling audio and video files, cover best practices, and provide an overview of currently available solutions to help overcome nuances with these unstructured data types.
September 12, 2023
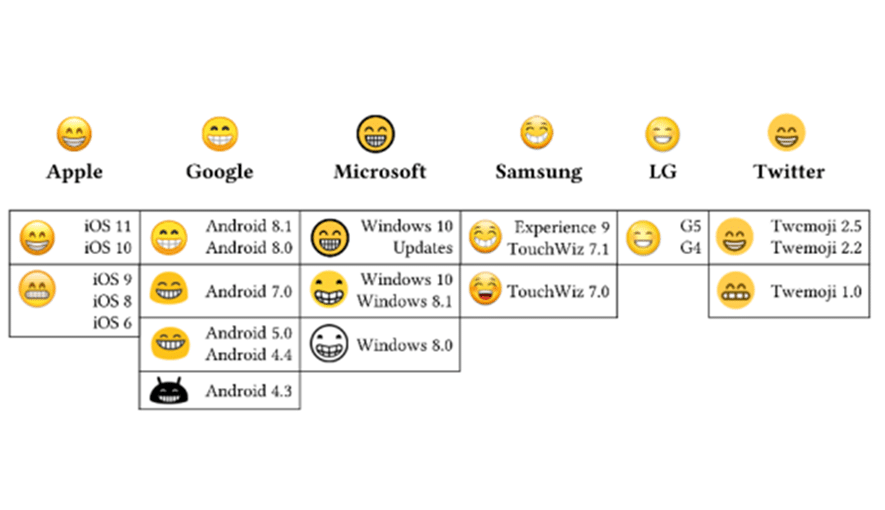
Emoji usage has grown significantly over the past few years since emoji characters provide people with the ability to express themselves in a clear and efficient way. These small, emotive characters—from ☂️to 😂 to 🤷 – represent the first language borne of the digital world that was originally designed to add emotional nuance to otherwise flat text.
July 4, 2023
Privilege logs are a critical component of eDiscovery that requires careful planning, analysis and detail in order to successfully complete. This process can be costly and time-consuming as specific requirements tend to vary by jurisdiction and on a case-by-case basis. As such, in this blog we would like to provide a brief overview of the privilege log process, discuss various privilege log types used today, and review how existing technologies can be leveraged to achieve efficiencies when constructing a privilege log.
May 15, 2023
The legal industry is undergoing transformational changes as aspects of information governance and eDiscovery are refined with new data governance solutions and technologies to address evolving business and regulatory requirements.
May 7, 2023
Messaging apps have become a ubiquitous form of communication, with billions of users worldwide. They have changed the way we communicate and share information with others in our personal lives and business, such that employees now routinely use messaging apps to conduct business. As the use of messaging apps has grown, so too has the need to collect data from these apps in a forensically sound manner from corporate-managed systems, as well as mobile devices for legal or investigatory reasons.
April 1, 2023
Organizations in Japan, and generally across Asia Pacific (APAC), have experienced a sharp increase in eDiscovery related work over the past several years due to a rise in cross-border litigations and investigations. It is more critical now than ever before to take stock of important considerations when evaluating and partnering with service providers that will guide and support your eDiscovery needs.
March 20, 2023
Organizations in Japan, and generally across Asia Pacific (APAC), have experienced a sharp increase in eDiscovery related work over the past several years due to a rise in cross-border litigations and investigations. It is more critical now than ever before to take stock of important considerations when evaluating and partnering with service providers that will guide and support your eDiscovery needs.